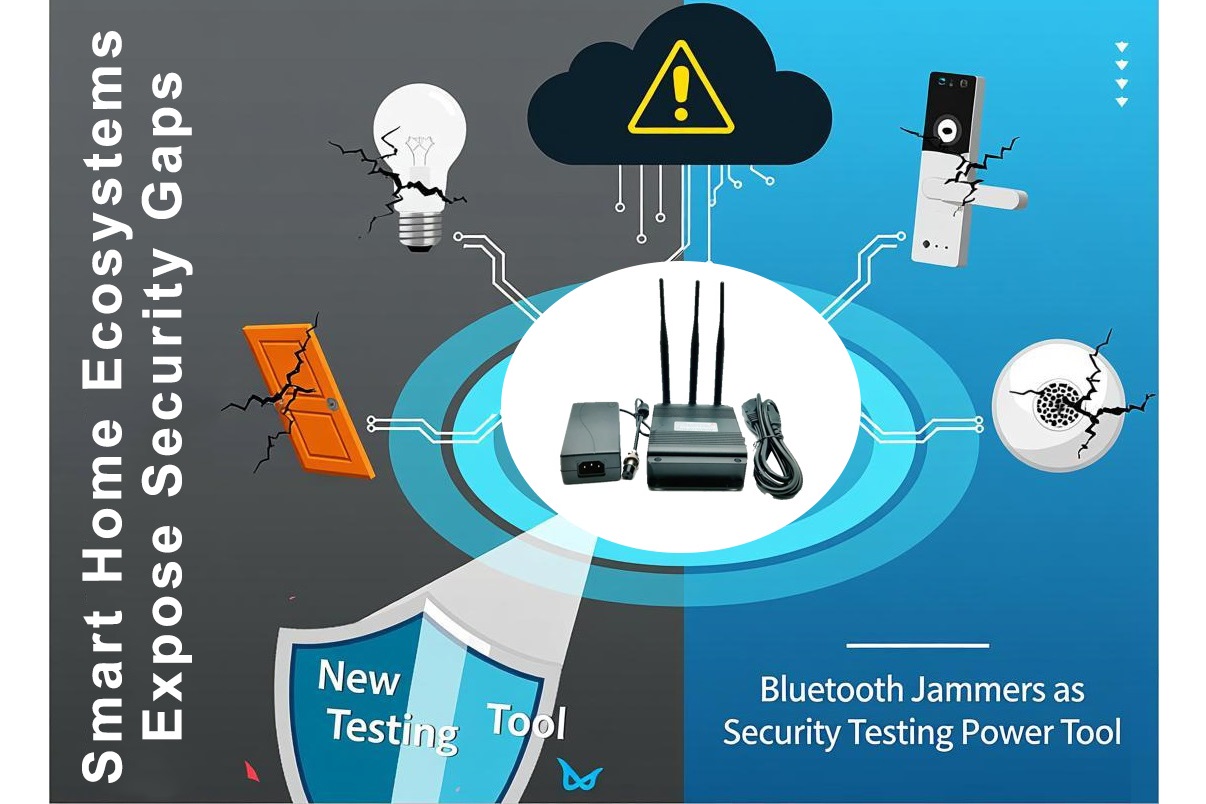
As smart homes evolve into always-connected ecosystems, convenience has quietly replaced caution. Wireless locks open with a tap, sensors report movement in milliseconds, and intelligent outlets respond to voice commands. But beneath this frictionless experience lies a rapidly expanding attack surface-one that security researchers say is far more fragile than most users realize.
Recent disclosures involving Bluetooth door locks, smart plugs, wireless motion sensors, and various low-power IoT modules highlight a troubling trend: many of these devices rely on unencrypted or weakly authenticated Bluetooth channels. As a result, a simple Bluetooth jammer-once seen as a niche RF tool-has now become a preferred instrument for cybersecurity teams, penetration testers, and even malicious actors.
The Smart Home Problem: Bluetooth Is Everywhere-And Often Underprotected
Bluetooth’s dominance is no coincidence. It is cheap, energy-efficient, and easy to integrate into embedded chipsets. For manufacturers racing toward mass adoption, it is the default wireless layer of choice.
But the same qualities that make Bluetooth ideal for consumer IoT also introduce security limitations:
1. Limited Processing Power → Weak Encryption
Many smart devices run on minimal microcontrollers that cannot support robust real-time cryptography. When corner-cutting happens, the first victim is secure key exchange.
2. Convenience Over Security
Devices prioritize quick pairing and instant responsiveness. This leaves little room for multi-layer authentication or frequency-hopping techniques that resist interference.
3. Predictable Communication Patterns
Bluetooth Low Energy (BLE) follows standardized advertising channels and predictable transmission cycles-ideal for targeted disruption by jammers.
These structural weaknesses explain why Bluetooth jammers have become essential for evaluating the resilience of smart home systems before attackers exploit the same flaws.
Why Bluetooth Jammers Became the “Dark Horse Tool” for Security Testing
Until recently, RF interference tools were considered “specialist equipment,” mainly used in controlled labs. But smart-home researchers now rely on Bluetooth Blockers for several reasons:
✔ 1. They Simulate Real-World Attacks That Software Tools Cannot
Software-based penetration tools can audit code, protocols, or encryption-but they cannot test:
- wireless channel reliability
- resilience to interference
- behavior under dropped or scrambled packets
- real-time fail-safe responses
Only RF hardware-especially Bluetooth Speaker Jammers can reproduce these physical-layer conditions.
✔ 2. They Expose Hidden Dependencies in Smart Home Ecosystems
A door lock might appear secure until someone tests how it behaves when:
- its BLE channel is saturated
- authentication packets arrive corrupted
- the hub cannot receive device status
In many cases, devices either freeze, unlock unintentionally, or revert to unsafe fallback modes-issues often invisible without RF testing.
✔ 3. Attackers Already Use RF Interference
From simple consumer jammers to advanced SDR-based disruptors, malicious interference is now cheap and accessible. Security teams must test against the same tools attackers use.
✔ 4. Bluetooth Jammers Simplify Multi-Device Stress Testing
Smart homes rarely contain one device-they host networks of 20-100+ nodes. Jammers allow:
- network-wide disruption testing
- mesh breakdown analysis
- hub overload simulation
This multi-point stress evaluation is impossible with single-device hacking tools.
Case Studies: Common Smart Home Vulnerabilities Exposed by Jamming Tests
🔹 Bluetooth Smart Locks
Jammer tests reveal:
- temporary communication loss often triggers “fail open” modes
- some models disable alarms when BLE signals drop
- pairing channels can be hijacked during interference windows
These issues turn what should be a security upgrade into a physical vulnerability.
🔹 Wireless Smart Plugs
During Bluetooth interference, some plugs:
- reboot unexpectedly
- revert to default “on” state
- fail to execute emergency-off commands
This poses serious risks for heaters, pumps, or appliances.
🔹 Motion Sensors & Alarms
Sensors relying on BLE to send alerts can be silenced for seconds-or indefinitely-if interference persists, providing attackers with hidden entry windows.
The Dual-Use Nature of Bluetooth Jammers
A Bluetooth jammer is neither inherently malicious nor inherently defensive. Like penetration frameworks or lock-picking tools, its purpose depends on who wields it.
Legitimate Uses Include:
- security research & penetration testing
- RF stability evaluation for manufacturers
- IoT product certification
- vulnerability audits before deployment
- forensic investigation of compromised devices
Smart home vendors increasingly use Bluetooth jammers during product development, not after flaws are exposed publicly.
But Misuse Exists:
Unsanctioned disruption of wireless signals is illegal in many jurisdictions. The value of Bluetooth jammers lies in controlled, authorized testing environments where they uncover vulnerabilities before real adversaries exploit them.
Why the Trend Will Continue: The Smart Home Security Gap Is Widening
As smart homes evolve toward:
- Matter & Thread ecosystems
- multi-protocol hubs
- AI-enhanced automation
- cloud-integrated device intelligence
Bluetooth will remain a foundational wireless layer. Yet devices are growing faster than security standards.
This imbalance ensures that Bluetooth jammers will become even more critical tools for:
- RF penetration testing labs
- IoT manufacturers
- enterprise security teams
- researchers tracking signal abuse
- government and critical-infra assessments
Because vulnerabilities in low-power wireless layers don’t just affect smart homes-they affect hospitals, factories, logistics systems, and autonomous devices.
Conclusion: Bluetooth Jammers Are Reshaping Smart Home Security Assessment
Smart home devices promise ease and automation, but their wireless foundations are far from airtight. As real-world disclosures show, many Bluetooth-enabled devices are vulnerable not only to logical attacks, but also to physical-layer interference.
This is why Bluetooth jammers have emerged as the unexpected “dark horse” tool for testing-compact, practical, and capable of revealing weaknesses that no software scanner can detect.
For manufacturers, ignoring RF security is no longer an option. For security teams, Bluetooth jammers are becoming mandatory equipment. And for consumers, understanding these vulnerabilities is essential to making safer choices in a hyperconnected home.