In the era of digital information explosion, we are increasingly relying on wireless networks and smart devices to work, live and communicate. But at the same time, problems such as privacy leakage, illegal monitoring and hacker intrusion are becoming more and more prominent. Especially in corporate offices, personal privacy spaces and public places, the existence of hidden cameras and unknown WiFi connections has caused many users to worry about information security. In order to solve these problems, network and wireless jammers have become an important tool to protect digital privacy.
This article will analyze in detail how to effectively protect personal and corporate privacy through technical means from the working principle of network blockers, the use scenarios of wireless signal blocker, hidden camera detection methods, and the feasibility of homemade jammers.
1. What are network and wireless signal jammers?
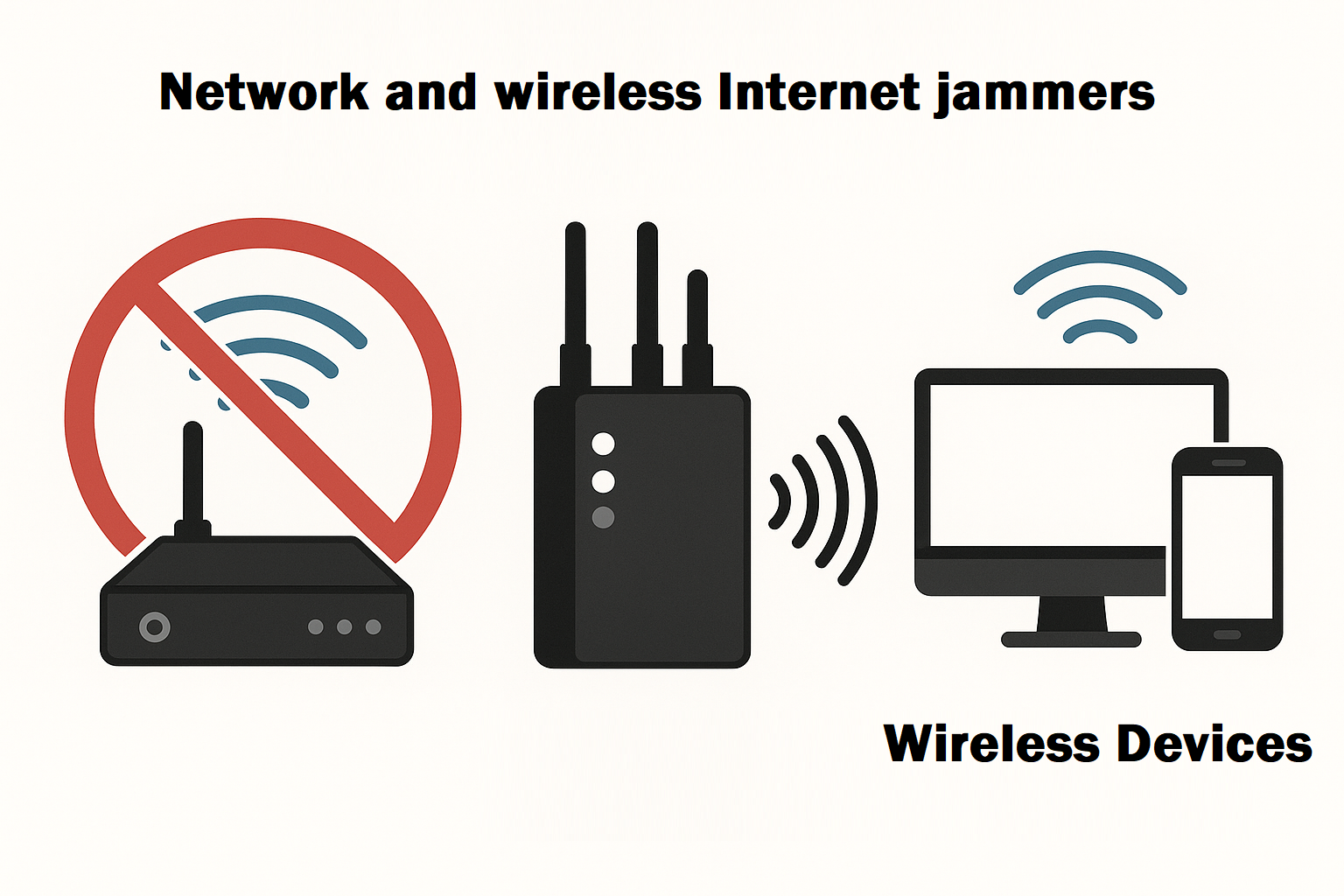
A Wi-Fi network blocker (or “Wireless Internet jammer”) is a device that interrupts wireless communications by emitting noise signals to a specified frequency range. Its main purpose is to prevent unauthorized third parties from accessing wireless networks or conducting remote communications, thereby effectively preventing hacker attacks, data leaks, and even remote monitoring and tracking.
The interference range of wireless signal blockers can be adjusted according to power. For example, low-power devices can only cover a radius of a few meters for home or office protection, while high-power devices can interfere with a range of tens of meters or even wider. It is very important to adjust the interference range because if the coverage range is too large, it may affect the normal communication of nearby legitimate devices and violate relevant radio management regulations.
2. Practical application scenarios of Wi-Fi frequency jamming equipment
Wireless network jammers can be used in the following scenarios under the premise of legality and compliance:
- Prevent illegal WiFi access: In commercial places, such as cafes and shared office spaces, prevent unfamiliar devices from connecting to internal WiFi to protect network security.
- Meeting and negotiation security: When companies conduct business confidential meetings, they can use jammers to block signal transmissions from possible listening devices or hidden cameras to ensure the privacy of conversations.
- Home privacy protection: In a home environment, jammers can effectively prevent smart devices (such as TVs and speakers) from being remotely controlled by hackers, while blocking illegal monitoring.
- High-security demand places: In places such as government agencies and financial institutions that have extremely high requirements for information confidentiality, jammers can be used as auxiliary tools for anti-eavesdropping and anti-leakage.
3. How to detect hidden cameras
Hidden cameras are one of the most common tools used in unauthorized surveillance and information theft. These cameras are often disguised as common items such as chargers, smoke detectors, sockets, and even screws, making them difficult to identify with the naked eye.
Here are some common methods for detecting hidden cameras:
1. Lens reflection detection method
By using a strong flashlight or the red light scanning function of a professional detector to illuminate the suspicious area, if the camera lens reflects light, it can be found.
2. Wireless signal scanning
Hidden cameras usually use WiFi, Bluetooth, or other wireless channels for image transmission. Portable detectors can scan these frequency bands to locate abnormal signal sources.
3. Heat source detection
Some advanced detectors are equipped with thermal imaging functions that can detect trace amounts of heat energy emitted by working cameras.
4. Mobile phone application assistance
Some mobile phone applications, combined with hardware sensors, can detect fluctuations in radio waves for discovering hidden devices, but the accuracy is low and suitable for simple preliminary screening.
4. Homemade hidden camera jammers: theory and reality
For economic considerations or interest-driven, some people will try to make their own wireless jammers to block surveillance cameras. In theory, homemade jammers are feasible, but there are multiple challenges in practice:
1. High technical threshold
Wireless Camera jammers involve complex knowledge such as RF circuit design, signal modulation, and power control. It is difficult to make them successfully without a certain foundation in electronic circuits.
2. Difficult to obtain materials and tools
The RF chips, antennas, signal amplifiers and other components required for production are not available everywhere, and the precision requirements are high.
3. Performance is far inferior to purchased commercial jammers
Even if they are successfully made, the interference range and stability of homemade jammers cannot be compared with purchased Wireless Internet jammer. They can only cover a very small range and are easily interfered or fail.
5. Future prospects: new directions for intelligent privacy protection
With the development of AI and the Internet of Things, traditional jamming equipment is also constantly evolving. Some high-end devices have integrated multi-band adaptive technology, automatic signal detection functions, and can even automatically turn on interference mode after detecting monitoring signals. At the same time, technologies such as smart camera recognition and sound recognition blocking are also under development.
For ordinary users, future privacy protection devices will be more “plug and play”, safe and compliant, and can effectively protect without professional knowledge. For example, portable devices with integrated camera detection, wireless interference and WiFi isolation functions may become mainstream.
Conclusion
In today’s highly developed information age, maintaining the information security of individuals and organizations is not only a technical issue, but also the awareness and ability that every digital citizen should have. By using the network and wireless signal jamming devices reasonably, we can effectively improve the security of the digital space. But remember: technical means must go hand in hand with laws and regulations, and reasonable use is the right way.
Do you also have concerns about privacy security? Maybe now is the time to equip your life or work environment with a set of smart privacy protection tools.