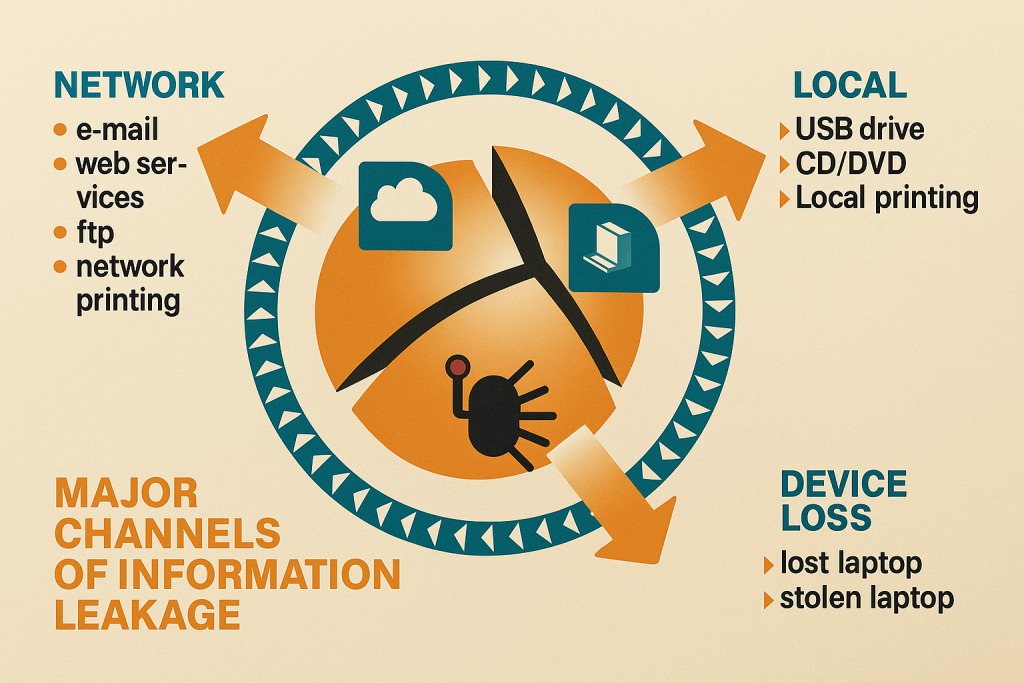
In today’s hyper-connected digital landscape, confidential information has become one of a company’s most valuable assets. From strategic documents and client databases to proprietary technologies, any data that fuels business success qualifies as a potential target for leakage.
Merely relying on advanced technology isn’t enough—the human element remains the weakest link in most security systems. To truly safeguard sensitive information, organizations must first understand the many ways it can be leaked—and how to stop it.
External Threats: When Technology Listens
Modern surveillance technology has evolved far beyond what traditional security measures can handle. Devices capable of eavesdropping on conversations and extracting data from electromagnetic fields are widely available and increasingly affordable.
Covert Listening Devices
Most bugging tools today fall into two categories:
- Concealed (Covert) Devices: These are disguised as everyday items such as pens, remote controls, wall outlets, or USB drives. They’re small, inconspicuous, and easy to plant.
- Unconcealed Devices: Typically small boxes, often hidden in bookshelves, air vents, or behind wall panels.
These tools often include a micro-sized wireless microphone, a dedicated receiver, and a self-contained power source, which may be rechargeable or battery-powered.
📡 Advanced versions use laser microphones to detect vibrations on window panes and convert them into readable audio—making even closed rooms vulnerable.
How to Detect and Prevent Surveillance
- RF (Radio Frequency) Scanners: Scan for unauthorized transmissions in office environments.
- Portable Bug Detectors (such as P-SCD): Ideal for personal use during meetings or in vehicles. Cost: $100–$300.
- White Noise Generators (such as J1000): Jam sensitive frequencies to disrupt eavesdropping.
- RF Shielding or Faraday Cages: Prevent wireless transmission entirely in high-security areas.
Internal Risks: The Human Weakness
While Hollywood loves to portray hackers breaking in from the outside, insiders cause far more damage. Employees, contractors, or service technicians often have direct or indirect access to valuable data—making them prime vectors for breaches.
Social Engineering & Insider Exploits
- Outsourced IT personnel or maintenance staff copying confidential data
- Employees transferring files via USB drives or personal cloud storage
- Staff taking databases when switching to a competitor
🔐 According to the 2024 Verizon Data Breach Investigations Report (DBIR), over 74% of breaches involve human error or insider threats.
Key Prevention Measures
- Non-Disclosure Agreements (NDAs) and Trade Secret Clauses for all staff and vendors
- Least Privilege Access: Grant only the minimum access required for a job
- Data Loss Prevention (DLP) software: Monitors USB activity, email attachments, and cloud uploads
- Audit logs & real-time alerts: Monitor employee actions involving sensitive files
- Proper offboarding: Immediately revoke credentials when employees leave
Technical Leaks: The Invisible Risks
Not all threats are tangible. Some exploit the side-effects of electronic operations, such as radiation or signal leaks.
Electromagnetic Side-Channel Attacks
Hackers can use special equipment to analyze electromagnetic emissions from CPUs or monitors to infer passwords or cryptographic keys. These attacks are difficult to detect and do not require direct system access.
Network-Based Exposures
- Transmission of sensitive files via unsecured HTTP or FTP
- Misconfigured cloud storage (e.g., public access to private buckets)
- Use of personal emails for corporate communications
Tech-Specific Defenses
- Enforce TLS/SSL encryption across all services
- Deploy Intrusion Detection/Prevention Systems (IDS/IPS)
- Implement Security Information and Event Management (SIEM) tools
- Limit installation of unauthorized third-party applications
Mobile & Offsite Vulnerabilities
Information is no longer confined to the office. Executives handle sensitive data while traveling, making mobile devices and remote work environments frequent targets.
Protecting Yourself in Transit
- Equip devices with Full Disk Encryption and Remote Wipe Capabilities
- Carry portable bug detectors or RF blockers
- Avoid using public Wi-Fi for accessing internal systems; always use enterprise-grade VPNs
Building a Holistic Information Security Framework
Securing information requires more than gadgets—it demands a coordinated human-tech-policy strategy:
- Security Training & Awareness: Educate staff on phishing, social engineering, and handling classified data
- Zero Trust Architecture: No one, not even internal users, is automatically trusted
- Behavioral Analytics (UEBA): AI-powered tools that detect unusual behavior and flag insider risks
Summary
Data leakage is not just a tech issue—it’s a human and organizational challenge.
Combining technological countermeasures, strong internal policies, and employee vigilance offers the most reliable path to safeguarding what matters most: your data.