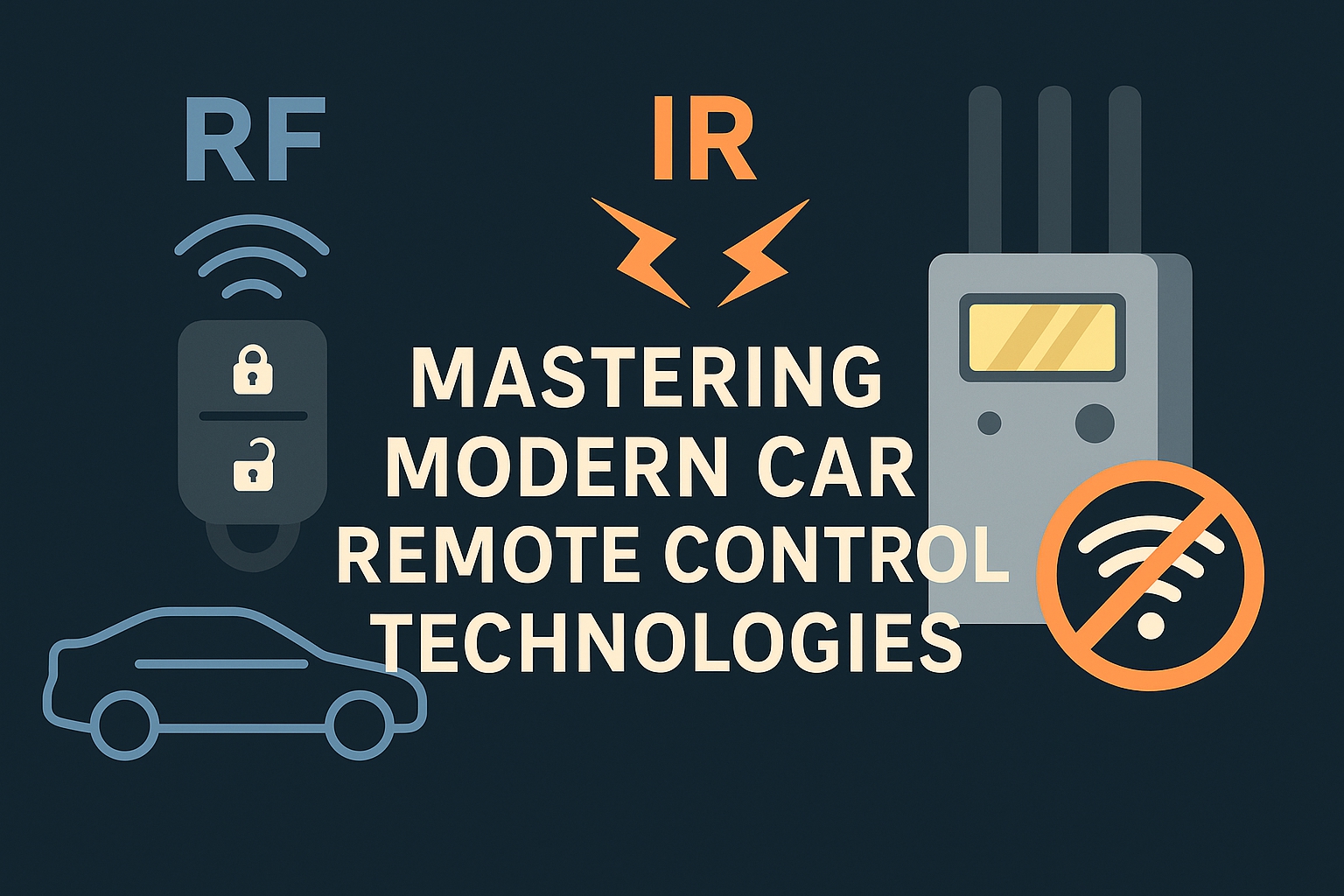
In today’s hyper-connected world, “remote control” means more than just changing TV channels. Your car key fob, garage door opener, smart air conditioner, and even your security cameras all rely on wireless remote technology – mainly infrared (IR) and radio frequency (RF) systems.
But as technology evolves, so do the risks of interference, hacking, and unwanted access. Understanding how these systems work – and how to protect or test them using signal blockers or jammers – is now essential knowledge for both consumers and professionals.
From Buttons to Bytes: How Modern Vehicle Remotes Work
Car remote technology has come a long way from simple lock/unlock buttons. Today’s smart key fobs communicate with your vehicle using RF signals, typically in the 315 MHz, 433 MHz, or 2.4 GHz frequency ranges. These signals can travel through walls, parked cars, and even people – allowing convenient keyless entry and remote start.
But here’s the catch: that same convenience opens the door to signal replay attacks and key cloning by malicious devices. In 2025, we’re seeing a rise in remote signal amplifiers and relay tools that can mimic your key’s signal from dozens of meters away – effectively unlocking your car without touching it.
That’s why security experts and developers now use RF signal jammers or analyzers to test the resilience of these systems against unauthorized access.
RF vs. Infrared – What’s the Real Difference?
| Feature | Infrared (IR) | Radio Frequency (RF) |
|---|---|---|
| Medium | Light wave | Radio wave |
| Transmission | Line of sight only | Can pass through walls and obstacles |
| Range | Short (a few meters) | Long (up to hundreds of meters) |
| Interference | Affected by sunlight and heat | Affected by WiFi, Bluetooth, and other RF devices |
| Security | Hard to intercept | Easier to intercept or jam |
Infrared remotes are old-school but reliable – they need a clear line of sight but offer excellent security and precision. RF remotes, on the other hand, dominate today’s tech market thanks to their long range and versatility. Everything from smart home systems to car remotes to Flipper Zero devices use RF signals to communicate efficiently.
The Hidden Power of Flipper Zero and Signal Analysis
If you’ve ever heard of the Flipper Zero, you know it’s like a Swiss army knife for wireless signals. It can both receive and transmit infrared and record or emulate RF signals, making it a favorite among cybersecurity professionals (and yes, hackers too).
Used correctly, tools like Flipper Zero are great for signal testing, frequency mapping, and security auditing – showing how easily common remotes can be intercepted or duplicated.
That’s also where signal jammers come into play – to block, test, or shield devices from unwanted transmission during research or privacy-sensitive operations.
How to Improve RF Jammer Range and Reliability
If you’re working with RF interference tools (legally and responsibly), performance depends on more than just power output. Here are expert-level tips to optimize jammer efficiency and coverage:
- Use the Correct Frequency Bands – Identify whether your target device uses 315 MHz, 433 MHz, or 2.4 GHz and adjust your jammer accordingly.
- Antenna Positioning Matters – Keep antennas upright and unobstructed; even small alignment changes can affect signal directionality.
- Avoid Metal Obstacles – Metal surfaces reflect and absorb RF waves, reducing effective range.
- Use Shielded Environments for Testing – Conduct tests in controlled areas to avoid disrupting other wireless devices.
- Temperature and Power Stability – Keep your jammer well-ventilated; heat buildup can degrade performance over time.
These factors can significantly boost your jammer’s efficiency, whether for lab testing, vehicle security research, or anti-spy signal blocking.
Signal Blocking and Privacy: The Invisible Defense
Wireless communication is convenient – but also inherently exposed. From keyless entry hacks to home automation breaches, the same technology that simplifies our lives can also compromise them.
That’s why professionals and privacy enthusiasts rely on signal blockers and RF jammers to:
- Prevent unauthorized data transmission
- Shield classified or confidential areas
- Conduct ethical penetration testing
- Simulate electronic interference environments safely
Remember: legality varies by region. Always ensure that signal blocking or jamming is used responsibly – for testing, research, or protection, not disruption.
Conclusion: Control the Signal, Control the Security
Infrared and RF technologies define the backbone of modern wireless control – from car keys to smart homes. But as our devices become smarter, so must our defense strategies.
Understanding how these frequencies interact, how they can be intercepted, and how to block them when necessary is key to maintaining true digital security.
After all, in a world where everything talks wirelessly, silence can be the ultimate protection.